Attacks on the IS-IS routing protocol
Last semester I took (together with Jonathan Kalechstein) a project in computer security under the supervision of Dr. Gabi Nakibly.
As part of the project we researched the IS-IS routing protocol and tried to see if we could come up with some new attacks or port known OSPF attacks to IS-IS.
We focused on 4 attacks, three of which are genuine, and one of them is an OSPF port. As of the genuine attacks, we created a PoC for one of them, while the other couple was not tested due to lack of support from Cisco IOS, or lack of time, hence they remain theoretical.
This blog post will begin with a short introduction on IS-IS and then dive into the attacks themselves.
The whitepaper itself (which contains the full details) can be found here, and the PoC code can be found here.
A very short background on IS-IS
IS-IS is a link-state routing protocol. In contrast to OSPF, IS-IS is carried over Layer-2, which is very limiting for remote attackers.
There are two routing levels: Level-1 (L1) and Level-2 (L2), and routers can be either L1, L2, or both (L1L2). L2 routers form the backbone of the network and they are contiguous. L1 routers are divided into areas. An L1 router sees the link states (adjacency + metric) of the L1 routers within its own area, and runs the Dijkstra SPF algorithm in order to form an optimal intra-area routing table. Inter-area messages are simply routed to the closest L1L2 router, so this results in suboptimal routing for the whole topology. L2 routers build an analogous L2 routing table using L2 link-states.

Two important aspects of IS-IS are the Hello protocol and Link-State updates.
The Hello protocol is used for forming an adjacency relation between two routers that share the same media (either LAN or Point-to-Point). The Hello message carries an important value called ‘Holding TIme’ which states how much time the sender wants the receiver to keep the adjacencies alive, and in contrast to OSPF, this can be asymmetric.
Link-State updates are used for distributing the information regarding adjacencies over the relevant topology. The data structure is called an LSP, and each router generates at least one. The LSP of some router contain the list of its adjacencies. In order to support versioning, the LSP carries two important attributes: sequence number and lifetime. An LSP with a bigger sequence number is newer. When the lifetime of an LSP becomes 0, it will soon be purged from the local LSP database. An LSP with lifetime set to zero, is called a purge LSP. When a router receives an LSP, it simply floods it over its other links, this is called the flooding process. Each time something changes in the topology, relevant LSPs are regenerated (updated) and flooded. If a router receives an LSP of which it is its source, and it is not coherent with its own database, it will fight back, meaning it will try to correct this behavior with a regenerated LSP, that contains a bigger sequence number but with the correct data. Obviously this behavior makes persistent attacks much harder to accomplish..
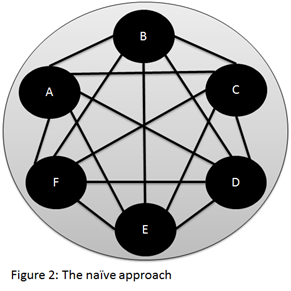
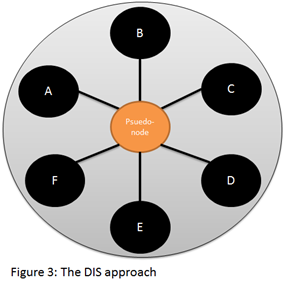
Back to the Hello protocol, resource consumption problem arises on LANs, as the naïve solution explained above would create O(n^2) adjacencies (fully connected mesh) for each LAN (memory consumption), and moreover, it creates O(n) updates for each change in the topology (network consumption). Life OSPF, IS-IS resolves this by elevating one router in the LAN to a special role called ‘Designated IS’ (‘DIS’ in short). The DIS router generates a special LSP, the psuedo-node LSP, and each router makes adjacency only with the pseudo-node. This behavior causes the number of adjacencies within the LAN to reduce to O(n) (star topology) and the number of updates per change to reduce to O(1). Problem solved! The DIS is elected using the Hello protocol; the Hello message carries a ‘priority’ attribute. The router with highest priority wins the election. As a tiebreaker the routers’ NSAP is used.
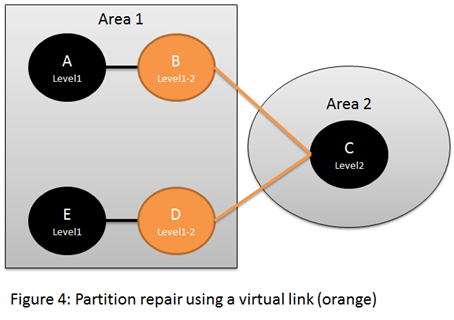
A cool feature of IS-IS (CLNP only) which is unfortunately not supported by IOS is the Partition Repair. If an area is split, two L1L2 routers are elected, one at each side. The elected routers create a virtual link over the backbone (the L2 network) in order to merge the area and overcome the split. Since IS-IS runs over Layer-2, one router cannot simply target IS-IS messages to a remote router; so in order to overcome that, IS-IS supports tunneling, over CLNP (Layer-3). The IS-IS message is simply encapsulated within a CLNP NPDU (with a special selector). When a router receives that message it decapsulates the IS-IS PDU and passes it to the relevant process.
We now have enough background to dive into the attacks.
Attack #1: One LAN, Multiple DISs
We assume the attacker can insert Hello messages to the LAN (i.e. has access to the media and holds the authentication key (if one is used)).
The local attacker sends spoofed unicast Hello messages from the current DIS to the other systems, with minimal priority. This causes the router with 2nd priority to be elected as DIS by other routers, while the current DIS assumes it is still the DIS. The router with the 2nd priority purges the pseudo-node LSP, however the current DIS fights back so this operation has no effect, so after this step, the LAN has 2 pseudo-node LSPs, one for the 1st priority system, and one for the 2nd. This process can be repeated until every router generates a pseudo-node for itself, i.e. the LAN becomes fully meshed, each node is connected to each other, hence the LAN is downgraded to the naïve approach which is discussed above.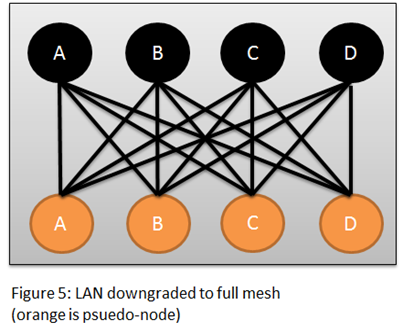
We confirmed this attack by our PoC on Cisco IOS 15.1. It is important the note that this attack is not persistent, and it remains as long as the DIS does not generate an Hello message (see whitepaper for more details)
Attack #2: One LAN, No DIS
This can be considered as the reverse of Attack #1. It is ported from OSPF. We again assume the attacker can insert Hello messages to the LAN and holds the authentication key (if one is used).
The attacker sends a unicast Hello message to the DIS on behalf of a phantom router, with higher priority. This causes the DIS to resign, and issue a purge LSP. However, other routers still assume the hasn’t changed (they haven’t processed the unicast Hello message), hence a new DIS is not elected. In contrast to OSPF, IS-IS supports asymmetric holding times, which makes the attack easier to maintain. This attack entirely breaks the LAN.
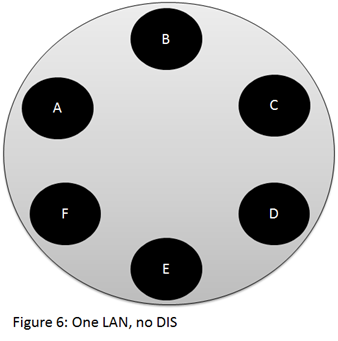
We created a functional PoC for this attack, and tested it on Cisco IOS 15.1. Interestingly we have seen that once the DIS resigns, it issues an Hello message, declaring the phantom router as the new DIS (using the relevant field in the Hello message). After processing this message, other LAN routers elected the phantom router to be the DIS although they are not adjacent.
Attack #3: Attacking Remote Routers via Virtual Links
It is a common belief that as IS-IS runs on top of Layer-2, an attacker cannot reach remote networks. When we discussed the Partition Repair function, we mentioned that a virtual link is created between two L2 routers. In effect, there is no tunnel establishment phase, there is no authentication; the virtual link is always there. One simply needs to encapsulate the IS-IS PDU within CLNP which specifies the destination, hence reaching remote systems is possible (at least on CLNP networks)..
Since Cisco IOS does not support this feature, we couldn’t verify the attack. We checked whether it decapsulates CLNP NPDUs either way but unfortunately that is not the case.
We hope that future implementations will take this vulnerability into consideration.
Attack #4: Avoiding Fight-back by Sending Unicast Link-State Updates
We assume the attacker can insert Link-State updates into the network.
According to the RFC, a router which receives an LSP will not flood it over the arriving circuit. Therefore, in certain topologies, an attacker can send false Link-State updates in unicast, on behalf of another router. The latter will never receive these messages and therefore will not fight back. For example, lets examine the following topology:
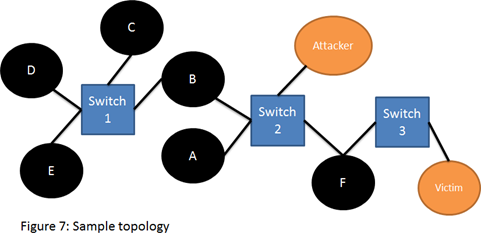
The attacker can send false Link-State update on behalf of ‘Victim’ to ‘B’ and ‘A’ in unicast. Since ‘F’ will not process these messages, and both ‘A’ and ‘B’ will not flood the LSP back into switch 2, ‘Victim’ will never see the malicious update and will not fight-back. Routers ‘A’, ‘B’, ‘C’, ‘D’ and ‘E’, will be infected with the malicious LSP.
Due to lack of time we didn’t verify this attack, so it remains theoretical.
As part of the project we researched the IS-IS routing protocol and tried to see if we could come up with some new attacks or port known OSPF attacks to IS-IS.
We focused on 4 attacks, three of which are genuine, and one of them is an OSPF port. As of the genuine attacks, we created a PoC for one of them, while the other couple was not tested due to lack of support from Cisco IOS, or lack of time, hence they remain theoretical.
This blog post will begin with a short introduction on IS-IS and then dive into the attacks themselves.
The whitepaper itself (which contains the full details) can be found here, and the PoC code can be found here.
A very short background on IS-IS
IS-IS is a link-state routing protocol. In contrast to OSPF, IS-IS is carried over Layer-2, which is very limiting for remote attackers.
There are two routing levels: Level-1 (L1) and Level-2 (L2), and routers can be either L1, L2, or both (L1L2). L2 routers form the backbone of the network and they are contiguous. L1 routers are divided into areas. An L1 router sees the link states (adjacency + metric) of the L1 routers within its own area, and runs the Dijkstra SPF algorithm in order to form an optimal intra-area routing table. Inter-area messages are simply routed to the closest L1L2 router, so this results in suboptimal routing for the whole topology. L2 routers build an analogous L2 routing table using L2 link-states.

Two important aspects of IS-IS are the Hello protocol and Link-State updates.
The Hello protocol is used for forming an adjacency relation between two routers that share the same media (either LAN or Point-to-Point). The Hello message carries an important value called ‘Holding TIme’ which states how much time the sender wants the receiver to keep the adjacencies alive, and in contrast to OSPF, this can be asymmetric.
Link-State updates are used for distributing the information regarding adjacencies over the relevant topology. The data structure is called an LSP, and each router generates at least one. The LSP of some router contain the list of its adjacencies. In order to support versioning, the LSP carries two important attributes: sequence number and lifetime. An LSP with a bigger sequence number is newer. When the lifetime of an LSP becomes 0, it will soon be purged from the local LSP database. An LSP with lifetime set to zero, is called a purge LSP. When a router receives an LSP, it simply floods it over its other links, this is called the flooding process. Each time something changes in the topology, relevant LSPs are regenerated (updated) and flooded. If a router receives an LSP of which it is its source, and it is not coherent with its own database, it will fight back, meaning it will try to correct this behavior with a regenerated LSP, that contains a bigger sequence number but with the correct data. Obviously this behavior makes persistent attacks much harder to accomplish..
Back to the Hello protocol, resource consumption problem arises on LANs, as the naïve solution explained above would create O(n^2) adjacencies (fully connected mesh) for each LAN (memory consumption), and moreover, it creates O(n) updates for each change in the topology (network consumption). Life OSPF, IS-IS resolves this by elevating one router in the LAN to a special role called ‘Designated IS’ (‘DIS’ in short). The DIS router generates a special LSP, the psuedo-node LSP, and each router makes adjacency only with the pseudo-node. This behavior causes the number of adjacencies within the LAN to reduce to O(n) (star topology) and the number of updates per change to reduce to O(1). Problem solved! The DIS is elected using the Hello protocol; the Hello message carries a ‘priority’ attribute. The router with highest priority wins the election. As a tiebreaker the routers’ NSAP is used.


A cool feature of IS-IS (CLNP only) which is unfortunately not supported by IOS is the Partition Repair. If an area is split, two L1L2 routers are elected, one at each side. The elected routers create a virtual link over the backbone (the L2 network) in order to merge the area and overcome the split. Since IS-IS runs over Layer-2, one router cannot simply target IS-IS messages to a remote router; so in order to overcome that, IS-IS supports tunneling, over CLNP (Layer-3). The IS-IS message is simply encapsulated within a CLNP NPDU (with a special selector). When a router receives that message it decapsulates the IS-IS PDU and passes it to the relevant process.

We now have enough background to dive into the attacks.
Attack #1: One LAN, Multiple DISs
We assume the attacker can insert Hello messages to the LAN (i.e. has access to the media and holds the authentication key (if one is used)).
The local attacker sends spoofed unicast Hello messages from the current DIS to the other systems, with minimal priority. This causes the router with 2nd priority to be elected as DIS by other routers, while the current DIS assumes it is still the DIS. The router with the 2nd priority purges the pseudo-node LSP, however the current DIS fights back so this operation has no effect, so after this step, the LAN has 2 pseudo-node LSPs, one for the 1st priority system, and one for the 2nd. This process can be repeated until every router generates a pseudo-node for itself, i.e. the LAN becomes fully meshed, each node is connected to each other, hence the LAN is downgraded to the naïve approach which is discussed above.

We confirmed this attack by our PoC on Cisco IOS 15.1. It is important the note that this attack is not persistent, and it remains as long as the DIS does not generate an Hello message (see whitepaper for more details)
Attack #2: One LAN, No DIS
This can be considered as the reverse of Attack #1. It is ported from OSPF. We again assume the attacker can insert Hello messages to the LAN and holds the authentication key (if one is used).
The attacker sends a unicast Hello message to the DIS on behalf of a phantom router, with higher priority. This causes the DIS to resign, and issue a purge LSP. However, other routers still assume the hasn’t changed (they haven’t processed the unicast Hello message), hence a new DIS is not elected. In contrast to OSPF, IS-IS supports asymmetric holding times, which makes the attack easier to maintain. This attack entirely breaks the LAN.

We created a functional PoC for this attack, and tested it on Cisco IOS 15.1. Interestingly we have seen that once the DIS resigns, it issues an Hello message, declaring the phantom router as the new DIS (using the relevant field in the Hello message). After processing this message, other LAN routers elected the phantom router to be the DIS although they are not adjacent.
Attack #3: Attacking Remote Routers via Virtual Links
It is a common belief that as IS-IS runs on top of Layer-2, an attacker cannot reach remote networks. When we discussed the Partition Repair function, we mentioned that a virtual link is created between two L2 routers. In effect, there is no tunnel establishment phase, there is no authentication; the virtual link is always there. One simply needs to encapsulate the IS-IS PDU within CLNP which specifies the destination, hence reaching remote systems is possible (at least on CLNP networks)..
Since Cisco IOS does not support this feature, we couldn’t verify the attack. We checked whether it decapsulates CLNP NPDUs either way but unfortunately that is not the case.
We hope that future implementations will take this vulnerability into consideration.
Attack #4: Avoiding Fight-back by Sending Unicast Link-State Updates
We assume the attacker can insert Link-State updates into the network.
According to the RFC, a router which receives an LSP will not flood it over the arriving circuit. Therefore, in certain topologies, an attacker can send false Link-State updates in unicast, on behalf of another router. The latter will never receive these messages and therefore will not fight back. For example, lets examine the following topology:

The attacker can send false Link-State update on behalf of ‘Victim’ to ‘B’ and ‘A’ in unicast. Since ‘F’ will not process these messages, and both ‘A’ and ‘B’ will not flood the LSP back into switch 2, ‘Victim’ will never see the malicious update and will not fight-back. Routers ‘A’, ‘B’, ‘C’, ‘D’ and ‘E’, will be infected with the malicious LSP.
Due to lack of time we didn’t verify this attack, so it remains theoretical.